The Six Main Causes of Corporate Breaches

Credentials

Unmanaged Network Ports

Software Updates

VPN Access
Unprotected Internet Exposure

Opening Apps to 3rd Parties
Breaches, Corporate or Local, Expose companies to:



Simplify and Secure Access to Resources with a Unified SaaS Platform
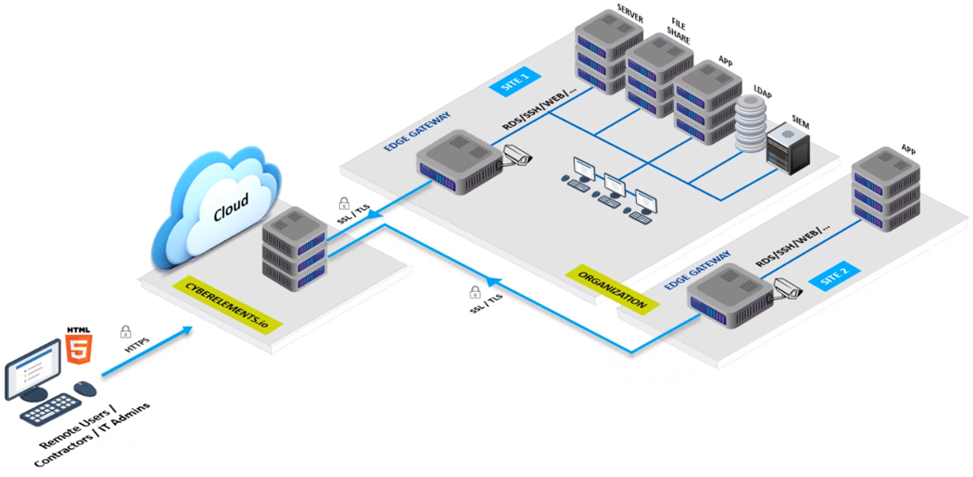
Access is granted to systems through the organizations entry point hosted in the cloud.
https://YourOrg.cyberelements.io
The Cyberelements Edge Gateway sits next to your resources, and manages access, and load.
Apps can be On-Premise, or in the cloud, they can be IT, Operational Technology or any mix of all 4.



